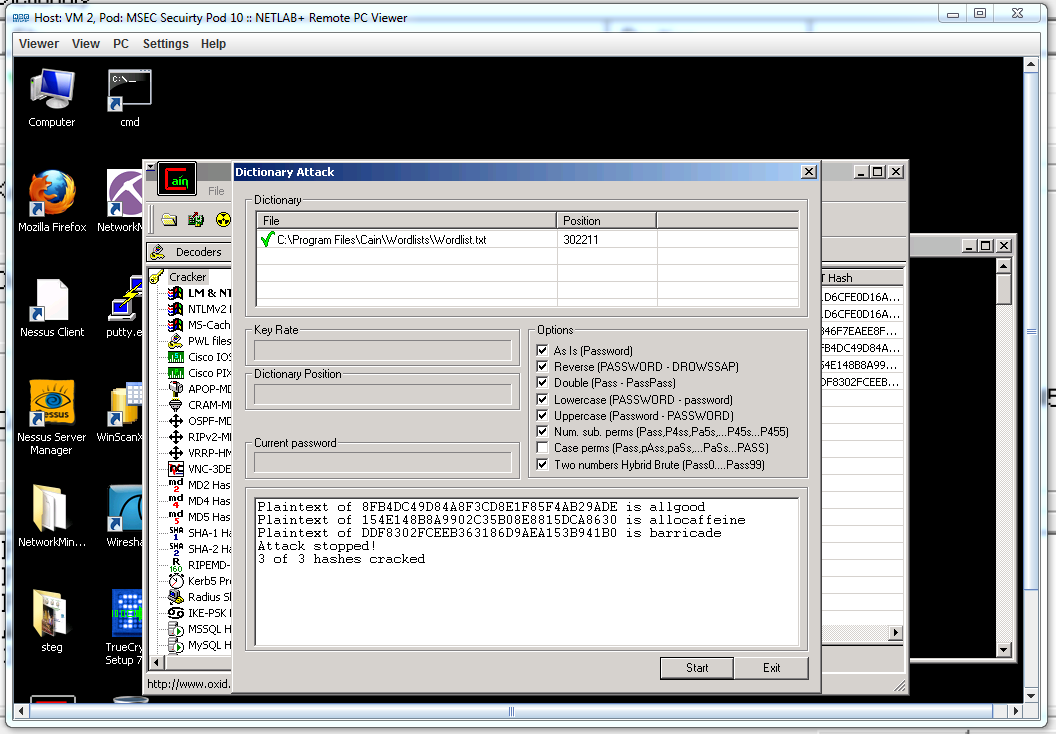
In this task we created a text file with a message in, we then used a hash calculation to create a hash for that message in both MD5 and SHA1. We then sent these text files over to another machine and calculated the hash of the transferred message and compared it to the original hash. If they were the same the message hadn't been tampered with if not it had. They were the same. We then changed the message in the text file and created another hash for it, compared it again to the original. This then showed how much they varied.
 |
| The new message hash compared to original |
1. What do you believe would happen if you had merely added a space character to the input file rather than the word “modified”?
The hash function would have still been different to the original
2. What are the differences between the MD5 and SHA1 algorithms?
SHA1 has a larger digest size and more rounds.
3. Choose two of the other hash algorithms available in the HashCalc application. Research them and compare them to MD5 and SHA1.
MD5- 64 bit, 64 rounds, digest size 128.
SHA1- 64 bit. 80 rounds, digest size 160.
Tiger- 64 bit, 24 rounds and the max digest size is 192, fast in software.
Panama- can be used as a stream cipher, digest size 256, 256 bit per block, doesn't have rounds, hashes every word not letter.
4. You will notice there are multiple SHA algorithms. What is the difference between SHA versions?
The difference between the SHA versions is the difference in output size, they increase in size down the list, the block size is bigger in the 384, 512 versions as are the rounds in them two versions. The increase in size means they are slower then SHA1.
5. What is another very common application where hash algorithms are used?
Hash algorithms are used to show integrity, so the message sent has the same hash as when sent, meaning the person receiving the message knows it hasn't been tampered with. Hashes are also used for integrity within a digital certificate so you know the person is who they say they are.
6. BONUS – What are some security concerns associated with the use of cryptographic hash functions?
Alot of the hash functions are broken for example MD4 and also it is suspected that the NSA have back doors into some of the current most used functions like MD5, if so then there is risk when using these hash functions. Also they are always susceptible to brute force attacks and with the growing power of home computers some of these functions will need to improve.
TASK 2:
In this task we created a message encrypted it and opened it up on the other machine and decrypted it on there with the result showing the same message that was encrypted.
 |
| Decrypting the message |
1. CrypTool supports a wide variety of modern and classic symmetric key algorithms. Research the Caesar and Vigenere ciphers and briefly discuss their history.
Caesar used substitution cipher so it was a fixed movement on the letter however Vigenere used they key word so there was no pattern there to determine a possible message.
2. What is the difference between the DES and 3DES algorithms?
3DES does the original DES algorithm three times. This means that it is much more secure. It has more bits and more rounds through the algorithm.
3. Explain how a brute force attack can be performed against an encrypted document.
They can try every possible combination on the encrypted message to get the actual message.
4. Research and discuss an example of a symmetric key algorithm for which flaws or weaknesses were discovered.
With symmetric keys both the key used to encrypt is the same used to decrypt so it is susceptible to man in the middle attacks as if they intercept the key being sent for the person to decrypt they can decrypt the message themselves.
5. BONUS – Describe three of the different modes with which AES can be utilized. What is the purpose of these modes?
TASK 3:
In this task we sent an asymmetric encrypted message to another machine and used a private key at the other end to decrypt the message. Using the RSA encryption method is more secure as the private key is different to the public key.
1. It was stated that asymmetric key algorithms often require significantly larger keys. What are the common key sizes for RSA?
2048 bits
2. Investigate and describe PKI and explain why it is significant in asymmetric key cryptography.
PKI is very significant in asymmetric key cryptography as it is the body that handles the distribution and upkeep of public keys and digital certificates throughput the world, they also handle situations where public keys become compromised and keep that situation from escalating to cause real damage. It provides trust to the person to another machine through a third party saying you can trust it.
3. Determine whether there are any known attacks on RSA and if so, briefly describe how they work.
Known attacks on RSA include wiener's attack which occurs when the private key is small. It uses a method of finding out the private key when it is of a small size and when the private key is found out all of the messages assigned to that private key can be read.
4. Locate and describe three other asymmetric encryption algorithms and include where they are commonly employed.
Diffie-Hellman- generally considered to be secure when an appropriate mathematical group is used. Usually not implemented on hardware.
Digital Signature Algorithm (DSA)- not as efficient as RSA for signature verification, limits the security to around only 80 bits, However, it is widely used and accepted as a good algorithm.
ElGamal- is based on the Diffie-Hellman key agreement. ElGamal is the predecessor of DSA.