In this task we used the john the ripper software to crack the other users we created's passwords. It took around 5 minutes to gain all of the passwords in clear text though brute force and dictionary attacks.
 |
| john the ripper software working through the users' passwords |
1. What is the command to add a group to the system in Linux?
addgroup 'groupname'
2. What is the command to give a user a password in Linux?
passwd 'user name' then wait for the prompt to add a password
3. What is the command to add a user to the system in Linux?
useradd 'username' and can include -g 'groupname'
4. Where is the user’s encrypted password hash stored on a Linux system?
shadow file
TASK 2:
In this task we used the metasploit software to gain the hashes within the exploited terminal, we then used these hashes in the john the ripper console line in the backtrack system to gain the passwords that the hashes represent in the windows 2003 terminal.
 |
| john the ripper using the hashes gained from the metasploit software to gain passwords |
1. How can you learn more information about a particular exploit?
info
2. What is the command to dump the password hashes in meterpreter?
hashdump
3. What port needs to be open in order to use the DCOM RPC exploit?
port 135
4. What directory is John the Ripper located in on BackTrack?
pentest/passwords/john/
TASK 3:
In this task we used cain to obtain the passwords of the three users we created with a dictionary attack using the ntlm because it is the windows 7 system that we were attacking.
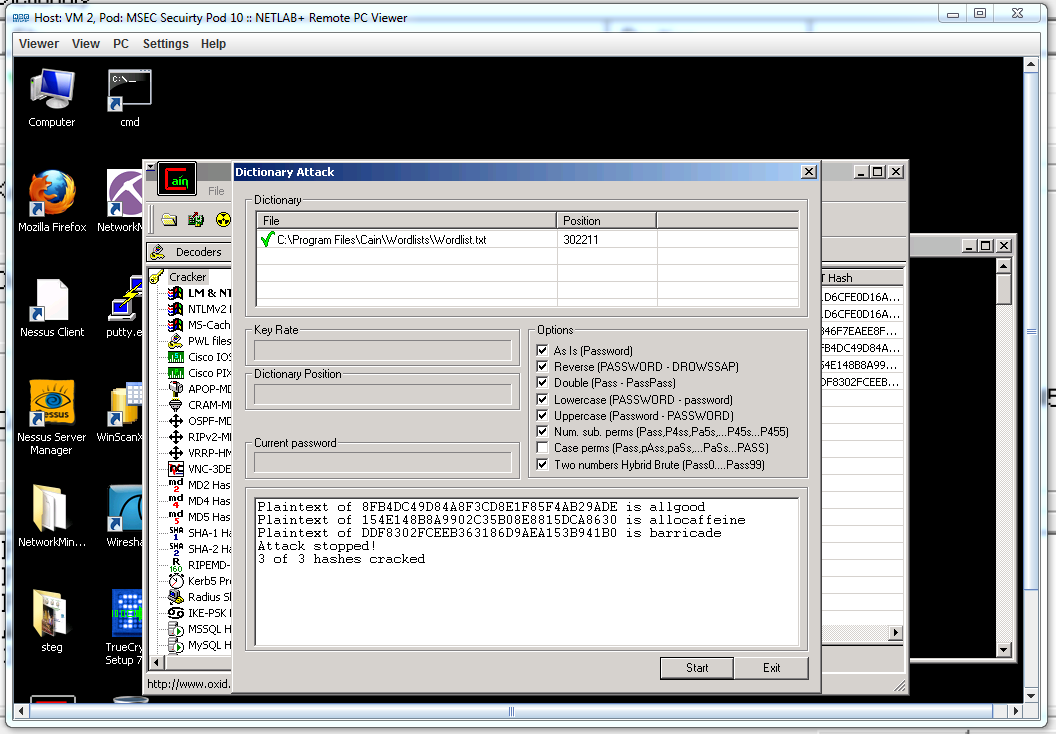 |
| This is cain using the dictionary attack to obtain the users 1, 2 and 3 passwords |
1. What Windows operating systems exclusively use the NTLM hash?
all windows operation systems after and including windows vista
2. What Windows operating systems use the LM hash?
all windows operating systems before windows vista
3. Where can someone obtain Cain?
http://www.oxid.it/ is where you can get the cain tool.
4. What is a disadvantage of using Cain?
it is classified as a virus by most AV vendors, admin rights needed also.
Appreciate your work. Thanks for everything you do :-)
ReplyDelete