TASK 1:
In this task we checked to see what ports were available and open on the network that the backtrack 5 system was on. After checking what was available we then started up metasploit and used the open port to get access to the vulnerable windows 2003 system.
1. What is the command to scan the 192.168.100.0/24 network for hosts?
nmap -sP 192.168.100.*
2. What is the command to scan 192.168.100.147 for open TCP ports?
nmap -O 192.168.100.201
3. How can you determine the operating system that the target system is running?
nmap -T4 -A -v 192.168.100.201
4. What command must be run before utilizing the db_autopwn command?
db_nmap 192.168.100.201 -p 21-445
TASK 2:
In this task we used the command prompts commands and copied them to the ir.txt file to log data attributed to the machine. This meant we could put in the time date system information into a text file and save that to the system.
1. What is the command to get important information about a Windows system?
systeminfo
2. What is the command to view active connections to a machine?
netstat –an | findstr “ESTABLISHED”
3. What is the command to list all of the processes on a machine?
pslist
4. What is the command to view the routing table?
netstat - r
TASK 3:
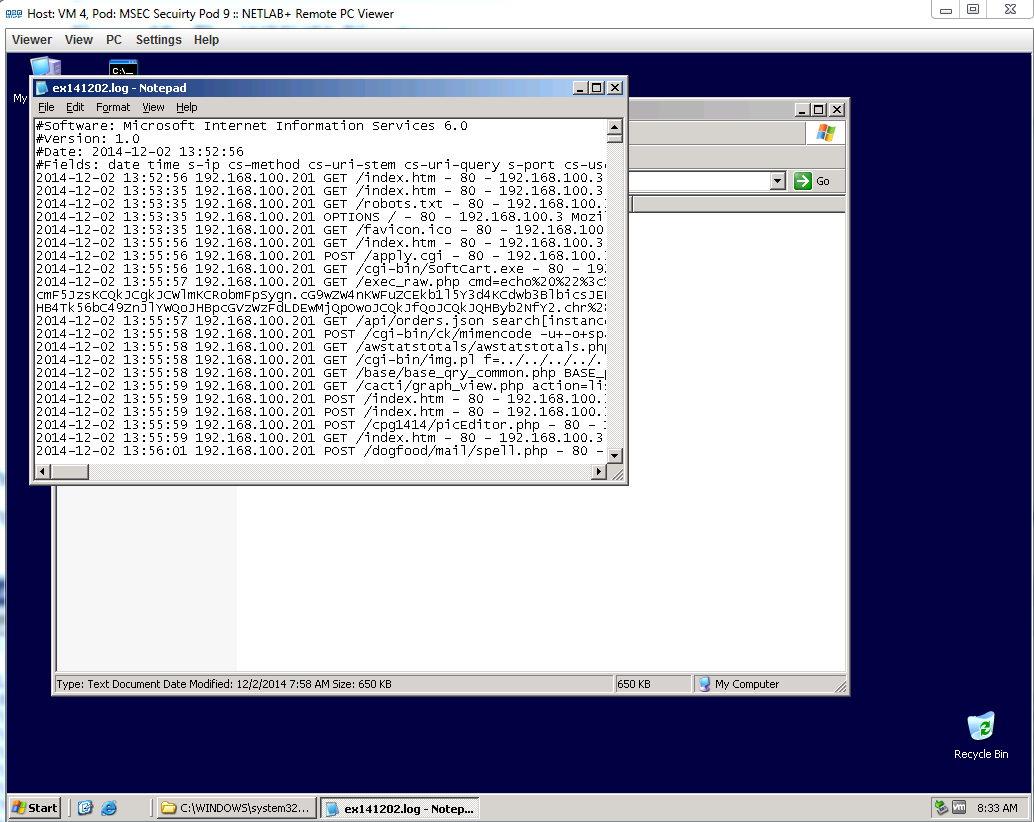
In this task we looked in the computers files to determine when and on what networks we were trying to be hacked.
1. Where are the log files stored on a Windows system?
system 32 log
2. Where are the FTP log files stored on a Windows system?
MSFTPSVC1
3. Where are the WWW log files stored on a Windows system?
W3SVC1 directory
4. Explain the naming format for log files within Windows.
They are organised by the date that they occurred


No comments:
Post a Comment