Digital Security
Monday, 9 May 2016
Unexpected Blog Views
Thanks everyone who is viewing my blog, I only did this to log the progress I made throughout a module I was studying at university and am in no way an expert in this field. I am however in my final year of university now and have published a game on the android google play store and due to the popularity of this blog am fixing a link to this as it is the only means of shameless advertising available to me. Thanks hope you enjoy:
https://play.google.com/store/apps/details?id=testing.testing.testing
or search: "The Grate Escape" on any android device made by Duke Student Games (the one with the cheese wedge)
Monday, 20 April 2015
Week 10 Lab 10
TASK 1:
In this task we viewed the security logs in the windows 2003 system. We then saved these logs to the desktop and cleared them so we could view what we were doing next. In the command prompt we then made a new user. After doing this we went into the event viewer and saw that making the user had been logged.
1. Name the three main Windows Event Logs.
Application log - issues with system software
System log - issues with system hardware
Security log - successful and failed attempts to access resources
2. Explain why saving Event Logs regularly is a good practice.
Logs can be deleted without the users knowledge, so its good to have evidence of them happening in any situation where you may need them after they have been erased.
3. Event Logs can be saved as which three different formats?
EVT
TXT
CSV
4. Adding a user account to the system will trigger an event in which log?
The security log under account management
TASK 2:
In this task we changed the audit policy on logging the failed attempts to log on to the administrative server. After making it log the failed log in attempts we updated the policies and then failed two log ins and then viewed them in the events security logs.
1. Which is more important, auditing for successes or failures?
In my opinion it is more important to log the failures as you can see if someone is attempting to get into your system who doesn't have permission, however if they are succeeding with their log in then that is a bigger issue but once they are in it is hard to stop them, stopping them is easier on the outside. Although you would want to know if someone is on the system so both are useful to have on.
2. Where do you go in Windows to examine the audit policy?
GP edit.msc
3. What are two ways that you can get to the Event Viewer in Windows?
run event viewer.msc
start>administrativeTools>eventviewer
4. What is the command line tool that can be used to update security settings?
gpupdate /force
TASK 3:
In this lab we used the backtrack 5 machine to access the windows 2003 machine and clear the logs on that machine.
1. What happens when the security log is cleared?
There is only one log left, it being the log telling you that all the logs are cleared.
2. What is the difference between the ClearLogs tool and the clearev command?
clearev clears all of the logs and ClearLogs allows you to clear individual logs in the system.
3. Why might a hacker clear the logs?
They clear the evidence that they were on the machine and it also prevents a forensic examiner from doing timeline analysis.
4. What would be an indicator that a hacker may have cleared one or more logs?
It logs that there has been a log cleared.
In this task we viewed the security logs in the windows 2003 system. We then saved these logs to the desktop and cleared them so we could view what we were doing next. In the command prompt we then made a new user. After doing this we went into the event viewer and saw that making the user had been logged.
1. Name the three main Windows Event Logs.
Application log - issues with system software
System log - issues with system hardware
Security log - successful and failed attempts to access resources
2. Explain why saving Event Logs regularly is a good practice.
Logs can be deleted without the users knowledge, so its good to have evidence of them happening in any situation where you may need them after they have been erased.
3. Event Logs can be saved as which three different formats?
EVT
TXT
CSV
4. Adding a user account to the system will trigger an event in which log?
The security log under account management
TASK 2:
In this task we changed the audit policy on logging the failed attempts to log on to the administrative server. After making it log the failed log in attempts we updated the policies and then failed two log ins and then viewed them in the events security logs.
1. Which is more important, auditing for successes or failures?
In my opinion it is more important to log the failures as you can see if someone is attempting to get into your system who doesn't have permission, however if they are succeeding with their log in then that is a bigger issue but once they are in it is hard to stop them, stopping them is easier on the outside. Although you would want to know if someone is on the system so both are useful to have on.
2. Where do you go in Windows to examine the audit policy?
GP edit.msc
3. What are two ways that you can get to the Event Viewer in Windows?
run event viewer.msc
start>administrativeTools>eventviewer
4. What is the command line tool that can be used to update security settings?
gpupdate /force
TASK 3:
In this lab we used the backtrack 5 machine to access the windows 2003 machine and clear the logs on that machine.
1. What happens when the security log is cleared?
There is only one log left, it being the log telling you that all the logs are cleared.
2. What is the difference between the ClearLogs tool and the clearev command?
clearev clears all of the logs and ClearLogs allows you to clear individual logs in the system.
3. Why might a hacker clear the logs?
They clear the evidence that they were on the machine and it also prevents a forensic examiner from doing timeline analysis.
4. What would be an indicator that a hacker may have cleared one or more logs?
It logs that there has been a log cleared.
Monday, 13 April 2015
Week 9 Lab 6
TASK 1:
In this task we checked to see what ports were available and open on the network that the backtrack 5 system was on. After checking what was available we then started up metasploit and used the open port to get access to the vulnerable windows 2003 system.
1. What is the command to scan the 192.168.100.0/24 network for hosts?
nmap -sP 192.168.100.*
2. What is the command to scan 192.168.100.147 for open TCP ports?
nmap -O 192.168.100.201
3. How can you determine the operating system that the target system is running?
nmap -T4 -A -v 192.168.100.201
4. What command must be run before utilizing the db_autopwn command?
db_nmap 192.168.100.201 -p 21-445
TASK 2:
In this task we used the command prompts commands and copied them to the ir.txt file to log data attributed to the machine. This meant we could put in the time date system information into a text file and save that to the system.
1. What is the command to get important information about a Windows system?
systeminfo
2. What is the command to view active connections to a machine?
netstat –an | findstr “ESTABLISHED”
3. What is the command to list all of the processes on a machine?
pslist
4. What is the command to view the routing table?
netstat - r
TASK 3:
In this task we looked in the computers files to determine when and on what networks we were trying to be hacked.
1. Where are the log files stored on a Windows system?
system 32 log
2. Where are the FTP log files stored on a Windows system?
MSFTPSVC1
3. Where are the WWW log files stored on a Windows system?
W3SVC1 directory
4. Explain the naming format for log files within Windows.
They are organised by the date that they occurred
In this task we checked to see what ports were available and open on the network that the backtrack 5 system was on. After checking what was available we then started up metasploit and used the open port to get access to the vulnerable windows 2003 system.
1. What is the command to scan the 192.168.100.0/24 network for hosts?
nmap -sP 192.168.100.*
2. What is the command to scan 192.168.100.147 for open TCP ports?
nmap -O 192.168.100.201
3. How can you determine the operating system that the target system is running?
nmap -T4 -A -v 192.168.100.201
4. What command must be run before utilizing the db_autopwn command?
db_nmap 192.168.100.201 -p 21-445
TASK 2:
In this task we used the command prompts commands and copied them to the ir.txt file to log data attributed to the machine. This meant we could put in the time date system information into a text file and save that to the system.
1. What is the command to get important information about a Windows system?
systeminfo
2. What is the command to view active connections to a machine?
netstat –an | findstr “ESTABLISHED”
3. What is the command to list all of the processes on a machine?
pslist
4. What is the command to view the routing table?
netstat - r
TASK 3:
In this task we looked in the computers files to determine when and on what networks we were trying to be hacked.
1. Where are the log files stored on a Windows system?
system 32 log
2. Where are the FTP log files stored on a Windows system?
MSFTPSVC1
3. Where are the WWW log files stored on a Windows system?
W3SVC1 directory
4. Explain the naming format for log files within Windows.
They are organised by the date that they occurred
Monday, 23 March 2015
week 8 Lab CNSS4011 LAB 3
TASK 1:
In this task we created a text file with a message in, we then used a hash calculation to create a hash for that message in both MD5 and SHA1. We then sent these text files over to another machine and calculated the hash of the transferred message and compared it to the original hash. If they were the same the message hadn't been tampered with if not it had. They were the same. We then changed the message in the text file and created another hash for it, compared it again to the original. This then showed how much they varied.
1. What do you believe would happen if you had merely added a space character to the input file rather than the word “modified”?
The hash function would have still been different to the original
2. What are the differences between the MD5 and SHA1 algorithms?
SHA1 has a larger digest size and more rounds.
3. Choose two of the other hash algorithms available in the HashCalc application. Research them and compare them to MD5 and SHA1.
MD5- 64 bit, 64 rounds, digest size 128.
SHA1- 64 bit. 80 rounds, digest size 160.
Tiger- 64 bit, 24 rounds and the max digest size is 192, fast in software.
Panama- can be used as a stream cipher, digest size 256, 256 bit per block, doesn't have rounds, hashes every word not letter.
4. You will notice there are multiple SHA algorithms. What is the difference between SHA versions?
The difference between the SHA versions is the difference in output size, they increase in size down the list, the block size is bigger in the 384, 512 versions as are the rounds in them two versions. The increase in size means they are slower then SHA1.
5. What is another very common application where hash algorithms are used?
Hash algorithms are used to show integrity, so the message sent has the same hash as when sent, meaning the person receiving the message knows it hasn't been tampered with. Hashes are also used for integrity within a digital certificate so you know the person is who they say they are.
6. BONUS – What are some security concerns associated with the use of cryptographic hash functions?
Alot of the hash functions are broken for example MD4 and also it is suspected that the NSA have back doors into some of the current most used functions like MD5, if so then there is risk when using these hash functions. Also they are always susceptible to brute force attacks and with the growing power of home computers some of these functions will need to improve.
TASK 2:
In this task we created a message encrypted it and opened it up on the other machine and decrypted it on there with the result showing the same message that was encrypted.
1. CrypTool supports a wide variety of modern and classic symmetric key algorithms. Research the Caesar and Vigenere ciphers and briefly discuss their history.
Caesar used substitution cipher so it was a fixed movement on the letter however Vigenere used they key word so there was no pattern there to determine a possible message.
2. What is the difference between the DES and 3DES algorithms?
3DES does the original DES algorithm three times. This means that it is much more secure. It has more bits and more rounds through the algorithm.
3. Explain how a brute force attack can be performed against an encrypted document.
They can try every possible combination on the encrypted message to get the actual message.
4. Research and discuss an example of a symmetric key algorithm for which flaws or weaknesses were discovered.
With symmetric keys both the key used to encrypt is the same used to decrypt so it is susceptible to man in the middle attacks as if they intercept the key being sent for the person to decrypt they can decrypt the message themselves.
5. BONUS – Describe three of the different modes with which AES can be utilized. What is the purpose of these modes?
TASK 3:
In this task we sent an asymmetric encrypted message to another machine and used a private key at the other end to decrypt the message. Using the RSA encryption method is more secure as the private key is different to the public key.
1. It was stated that asymmetric key algorithms often require significantly larger keys. What are the common key sizes for RSA?
2048 bits
2. Investigate and describe PKI and explain why it is significant in asymmetric key cryptography.
PKI is very significant in asymmetric key cryptography as it is the body that handles the distribution and upkeep of public keys and digital certificates throughput the world, they also handle situations where public keys become compromised and keep that situation from escalating to cause real damage. It provides trust to the person to another machine through a third party saying you can trust it.
3. Determine whether there are any known attacks on RSA and if so, briefly describe how they work.
Known attacks on RSA include wiener's attack which occurs when the private key is small. It uses a method of finding out the private key when it is of a small size and when the private key is found out all of the messages assigned to that private key can be read.
4. Locate and describe three other asymmetric encryption algorithms and include where they are commonly employed.
Diffie-Hellman- generally considered to be secure when an appropriate mathematical group is used. Usually not implemented on hardware.
Digital Signature Algorithm (DSA)- not as efficient as RSA for signature verification, limits the security to around only 80 bits, However, it is widely used and accepted as a good algorithm.
ElGamal- is based on the Diffie-Hellman key agreement. ElGamal is the predecessor of DSA.
In this task we created a text file with a message in, we then used a hash calculation to create a hash for that message in both MD5 and SHA1. We then sent these text files over to another machine and calculated the hash of the transferred message and compared it to the original hash. If they were the same the message hadn't been tampered with if not it had. They were the same. We then changed the message in the text file and created another hash for it, compared it again to the original. This then showed how much they varied.
 |
| The new message hash compared to original |
1. What do you believe would happen if you had merely added a space character to the input file rather than the word “modified”?
The hash function would have still been different to the original
2. What are the differences between the MD5 and SHA1 algorithms?
SHA1 has a larger digest size and more rounds.
3. Choose two of the other hash algorithms available in the HashCalc application. Research them and compare them to MD5 and SHA1.
MD5- 64 bit, 64 rounds, digest size 128.
SHA1- 64 bit. 80 rounds, digest size 160.
Tiger- 64 bit, 24 rounds and the max digest size is 192, fast in software.
Panama- can be used as a stream cipher, digest size 256, 256 bit per block, doesn't have rounds, hashes every word not letter.
4. You will notice there are multiple SHA algorithms. What is the difference between SHA versions?
The difference between the SHA versions is the difference in output size, they increase in size down the list, the block size is bigger in the 384, 512 versions as are the rounds in them two versions. The increase in size means they are slower then SHA1.
5. What is another very common application where hash algorithms are used?
Hash algorithms are used to show integrity, so the message sent has the same hash as when sent, meaning the person receiving the message knows it hasn't been tampered with. Hashes are also used for integrity within a digital certificate so you know the person is who they say they are.
6. BONUS – What are some security concerns associated with the use of cryptographic hash functions?
Alot of the hash functions are broken for example MD4 and also it is suspected that the NSA have back doors into some of the current most used functions like MD5, if so then there is risk when using these hash functions. Also they are always susceptible to brute force attacks and with the growing power of home computers some of these functions will need to improve.
TASK 2:
In this task we created a message encrypted it and opened it up on the other machine and decrypted it on there with the result showing the same message that was encrypted.
 |
| Decrypting the message |
1. CrypTool supports a wide variety of modern and classic symmetric key algorithms. Research the Caesar and Vigenere ciphers and briefly discuss their history.
Caesar used substitution cipher so it was a fixed movement on the letter however Vigenere used they key word so there was no pattern there to determine a possible message.
2. What is the difference between the DES and 3DES algorithms?
3DES does the original DES algorithm three times. This means that it is much more secure. It has more bits and more rounds through the algorithm.
3. Explain how a brute force attack can be performed against an encrypted document.
They can try every possible combination on the encrypted message to get the actual message.
4. Research and discuss an example of a symmetric key algorithm for which flaws or weaknesses were discovered.
With symmetric keys both the key used to encrypt is the same used to decrypt so it is susceptible to man in the middle attacks as if they intercept the key being sent for the person to decrypt they can decrypt the message themselves.
5. BONUS – Describe three of the different modes with which AES can be utilized. What is the purpose of these modes?
TASK 3:
In this task we sent an asymmetric encrypted message to another machine and used a private key at the other end to decrypt the message. Using the RSA encryption method is more secure as the private key is different to the public key.
1. It was stated that asymmetric key algorithms often require significantly larger keys. What are the common key sizes for RSA?
2048 bits
2. Investigate and describe PKI and explain why it is significant in asymmetric key cryptography.
PKI is very significant in asymmetric key cryptography as it is the body that handles the distribution and upkeep of public keys and digital certificates throughput the world, they also handle situations where public keys become compromised and keep that situation from escalating to cause real damage. It provides trust to the person to another machine through a third party saying you can trust it.
3. Determine whether there are any known attacks on RSA and if so, briefly describe how they work.
Known attacks on RSA include wiener's attack which occurs when the private key is small. It uses a method of finding out the private key when it is of a small size and when the private key is found out all of the messages assigned to that private key can be read.
4. Locate and describe three other asymmetric encryption algorithms and include where they are commonly employed.
Diffie-Hellman- generally considered to be secure when an appropriate mathematical group is used. Usually not implemented on hardware.
Digital Signature Algorithm (DSA)- not as efficient as RSA for signature verification, limits the security to around only 80 bits, However, it is widely used and accepted as a good algorithm.
ElGamal- is based on the Diffie-Hellman key agreement. ElGamal is the predecessor of DSA.
Monday, 16 March 2015
Week 7 Lab 12
TASK 1:
In this task we used the nmap command to view the available commands within this command and also used nmap on the command line to view the possible hosts on the network. We used zenmap to have a GUI representation of the scan we performed to view the ports available.
1. Why is nmap useful for people working in the field of Information Assurance?
So the security professionals can see if they are at risk of attacks and patch the possible places for attacks before being attacked
2. What is the best way to find out all of the available switches for nmap?
nmap
3. How can you perform a ping scan to determine alive hosts using nmap?
nmap –sP 10.10.19.*
4. What is the syntax to scan a remote machine for open UDP ports?
nmap –sU 10.10.19.202
5. What is the syntax to scan a remote machine for open TCP ports?
nmap –sT 10.10.19.202
TASK 2:
In this task we used the nessus server to identify holes in our system making them easier to solve when trying to fix them. We checked if the nessus server was available to use then started it up, we then used its scan function to find any vulnerabilities. We then viewed these vulnerabilities within nessus and it gave us information on the current hole and options on how to deal with it.
1. Why do you need to be cautious when initiating a Nessus scan?
It can cause your computer to crash
2. What is the command to start the Nessus server?
/etc/init.d/nessusd start
3. Which command can be used to verify that the Nessus server is running?
netstat -tanp
4. Is it possible to run the Nessus client and server on the same machine?
they don't have to but they can
TASK 3:
In this task we used the metaspoilt command and within that meterpreter to find a possible machine to hack into and add a user within that system from your own command line.
1. What is the command used to show all Windows exploits in Metasploit?
search exploits windows
2. What is the command used to show all Macintosh exploits in Metasploit?
search exploits osx
3. How can you learn more information about a particular exploit?
info windows/dcerpc/ms03_026_dcom
4. Launch msfconsole again. Use the banner command until you are able to get the picture of the cow. Type exit to leave the msfconsole environment.
In this task we used the nmap command to view the available commands within this command and also used nmap on the command line to view the possible hosts on the network. We used zenmap to have a GUI representation of the scan we performed to view the ports available.
 |
| Zenmap showing available hosts/ports |
1. Why is nmap useful for people working in the field of Information Assurance?
So the security professionals can see if they are at risk of attacks and patch the possible places for attacks before being attacked
2. What is the best way to find out all of the available switches for nmap?
nmap
3. How can you perform a ping scan to determine alive hosts using nmap?
nmap –sP 10.10.19.*
4. What is the syntax to scan a remote machine for open UDP ports?
nmap –sU 10.10.19.202
5. What is the syntax to scan a remote machine for open TCP ports?
nmap –sT 10.10.19.202
TASK 2:
In this task we used the nessus server to identify holes in our system making them easier to solve when trying to fix them. We checked if the nessus server was available to use then started it up, we then used its scan function to find any vulnerabilities. We then viewed these vulnerabilities within nessus and it gave us information on the current hole and options on how to deal with it.
 |
| finished nessus scan report |
It can cause your computer to crash
2. What is the command to start the Nessus server?
/etc/init.d/nessusd start
3. Which command can be used to verify that the Nessus server is running?
netstat -tanp
4. Is it possible to run the Nessus client and server on the same machine?
they don't have to but they can
TASK 3:
In this task we used the metaspoilt command and within that meterpreter to find a possible machine to hack into and add a user within that system from your own command line.
1. What is the command used to show all Windows exploits in Metasploit?
search exploits windows
2. What is the command used to show all Macintosh exploits in Metasploit?
search exploits osx
3. How can you learn more information about a particular exploit?
info windows/dcerpc/ms03_026_dcom
4. Launch msfconsole again. Use the banner command until you are able to get the picture of the cow. Type exit to leave the msfconsole environment.
 |
| Cow Banner |
Monday, 9 March 2015
Week 6 Lab 11
TASK 1:
In this task we used the john the ripper software to crack the other users we created's passwords. It took around 5 minutes to gain all of the passwords in clear text though brute force and dictionary attacks.
1. What is the command to add a group to the system in Linux?
addgroup 'groupname'
2. What is the command to give a user a password in Linux?
passwd 'user name' then wait for the prompt to add a password
3. What is the command to add a user to the system in Linux?
useradd 'username' and can include -g 'groupname'
4. Where is the user’s encrypted password hash stored on a Linux system?
shadow file
TASK 2:
In this task we used the metasploit software to gain the hashes within the exploited terminal, we then used these hashes in the john the ripper console line in the backtrack system to gain the passwords that the hashes represent in the windows 2003 terminal.
1. How can you learn more information about a particular exploit?
info
2. What is the command to dump the password hashes in meterpreter?
hashdump
3. What port needs to be open in order to use the DCOM RPC exploit?
port 135
4. What directory is John the Ripper located in on BackTrack?
pentest/passwords/john/
TASK 3:
In this task we used cain to obtain the passwords of the three users we created with a dictionary attack using the ntlm because it is the windows 7 system that we were attacking.
1. What Windows operating systems exclusively use the NTLM hash?
all windows operation systems after and including windows vista
2. What Windows operating systems use the LM hash?
all windows operating systems before windows vista
3. Where can someone obtain Cain?
http://www.oxid.it/ is where you can get the cain tool.
4. What is a disadvantage of using Cain?
it is classified as a virus by most AV vendors, admin rights needed also.
In this task we used the john the ripper software to crack the other users we created's passwords. It took around 5 minutes to gain all of the passwords in clear text though brute force and dictionary attacks.
 |
| john the ripper software working through the users' passwords |
1. What is the command to add a group to the system in Linux?
addgroup 'groupname'
2. What is the command to give a user a password in Linux?
passwd 'user name' then wait for the prompt to add a password
3. What is the command to add a user to the system in Linux?
useradd 'username' and can include -g 'groupname'
4. Where is the user’s encrypted password hash stored on a Linux system?
shadow file
TASK 2:
In this task we used the metasploit software to gain the hashes within the exploited terminal, we then used these hashes in the john the ripper console line in the backtrack system to gain the passwords that the hashes represent in the windows 2003 terminal.
 |
| john the ripper using the hashes gained from the metasploit software to gain passwords |
1. How can you learn more information about a particular exploit?
info
2. What is the command to dump the password hashes in meterpreter?
hashdump
3. What port needs to be open in order to use the DCOM RPC exploit?
port 135
4. What directory is John the Ripper located in on BackTrack?
pentest/passwords/john/
TASK 3:
In this task we used cain to obtain the passwords of the three users we created with a dictionary attack using the ntlm because it is the windows 7 system that we were attacking.
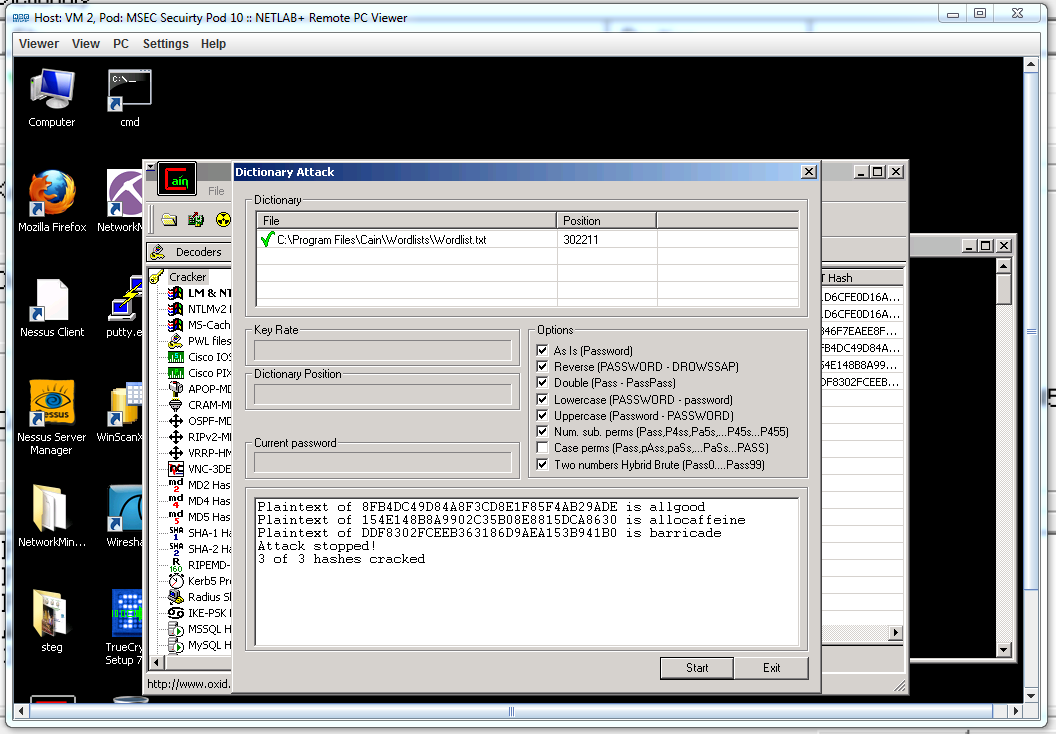 |
| This is cain using the dictionary attack to obtain the users 1, 2 and 3 passwords |
1. What Windows operating systems exclusively use the NTLM hash?
all windows operation systems after and including windows vista
2. What Windows operating systems use the LM hash?
all windows operating systems before windows vista
3. Where can someone obtain Cain?
http://www.oxid.it/ is where you can get the cain tool.
4. What is a disadvantage of using Cain?
it is classified as a virus by most AV vendors, admin rights needed also.
Monday, 2 March 2015
Week 5 Lab 15
TASK 1:
In this task we used the linux machine command line to create two different groups sesame street and Simpsons and then create users within them groups. We then added passwords to the created users and viewed the users encrypted hash on the shadow file.
1. What is the command to add a group to the system in Linux?
groupadd 'groupname'
2. What is the command to give a user a password in Linux?
passwd 'username' then write the password twice.
3. What is the command to add a user to the system in Linux?
useradd 'username' -g 'groupname'
4. Where is the user’s encrypted password hash stored on a Linux system?
cat /etc/shadow
TASK 2:
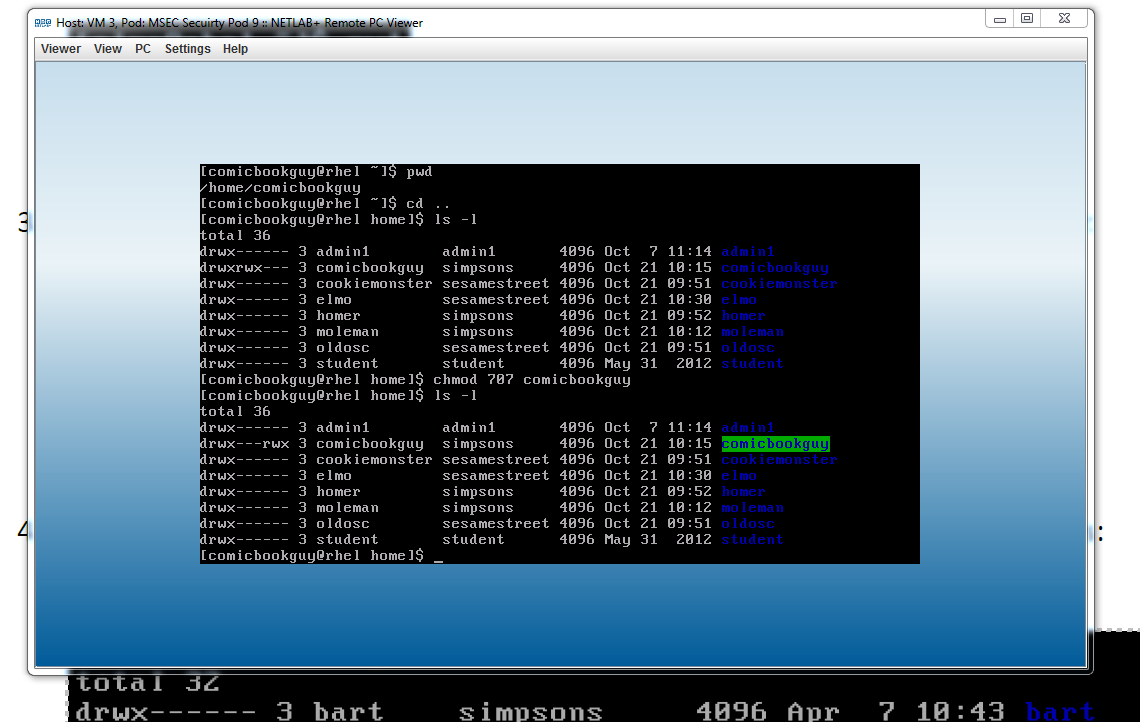
In this task we used the command line to login with a different user, not with the root user and seeing what the user has access to. We logged in with moleman and couldn't access comicbookguy's information. However when we logged into comicbookguy's account and made the other users of the same group able to access (write read and execute) some information. We then went into moleman's account and accessed comicbookguy's location within the system.
1. What is the command to give the group read and write permissions for the comicbookguy folder, within the home directory using symbolic permissions?
chmod g+rw comicbookguy
2. What is the command to give others read permissions for the comicbookguy folder, within the home directory using symbolic permissions?
chmod o+r comicbookguy
3. What is the command to take away the read permissions for group for the comicbookguy folder, within the home directory using symbolic permissions?
chmod g-r comicbookguy
4. What is the command to take away the read and execute permissions for the others for the comicbookguy folder, within the home directory using symbolic permissions?
chmod o-rx comicbookguy
TASK 3:
In this task we used the number syntax called absolute permissions to add read write and execute options on the user account to the other users on the system and not just the ones in the group.
1. What is the command to give the user, group, and others read and write permissions for the comicbookguy folder, within the home directory using absolute permissions?
chmod 666 comicbookguy
2. What is the command to give the user, group, and others read permissions for the comicbookguy folder, within the home directory using absolute permissions?
chmod 444 comicbookguy
3. What is the command to give read and execute permissions the user, group, and others for the comicbookguy folder, within the home directory using absolute permissions?
chmod 555 comicbookguy
4. What is the command to give read, write, and execute permissions the user, group, and others for the comicbookguy folder, within the home directory using absolute permissions?
chmod 777 comicbookguy
In this task we used the linux machine command line to create two different groups sesame street and Simpsons and then create users within them groups. We then added passwords to the created users and viewed the users encrypted hash on the shadow file.
 |
| The shadow file with the hash value |
1. What is the command to add a group to the system in Linux?
groupadd 'groupname'
2. What is the command to give a user a password in Linux?
passwd 'username' then write the password twice.
3. What is the command to add a user to the system in Linux?
useradd 'username' -g 'groupname'
4. Where is the user’s encrypted password hash stored on a Linux system?
cat /etc/shadow
TASK 2:
In this task we used the command line to login with a different user, not with the root user and seeing what the user has access to. We logged in with moleman and couldn't access comicbookguy's information. However when we logged into comicbookguy's account and made the other users of the same group able to access (write read and execute) some information. We then went into moleman's account and accessed comicbookguy's location within the system.
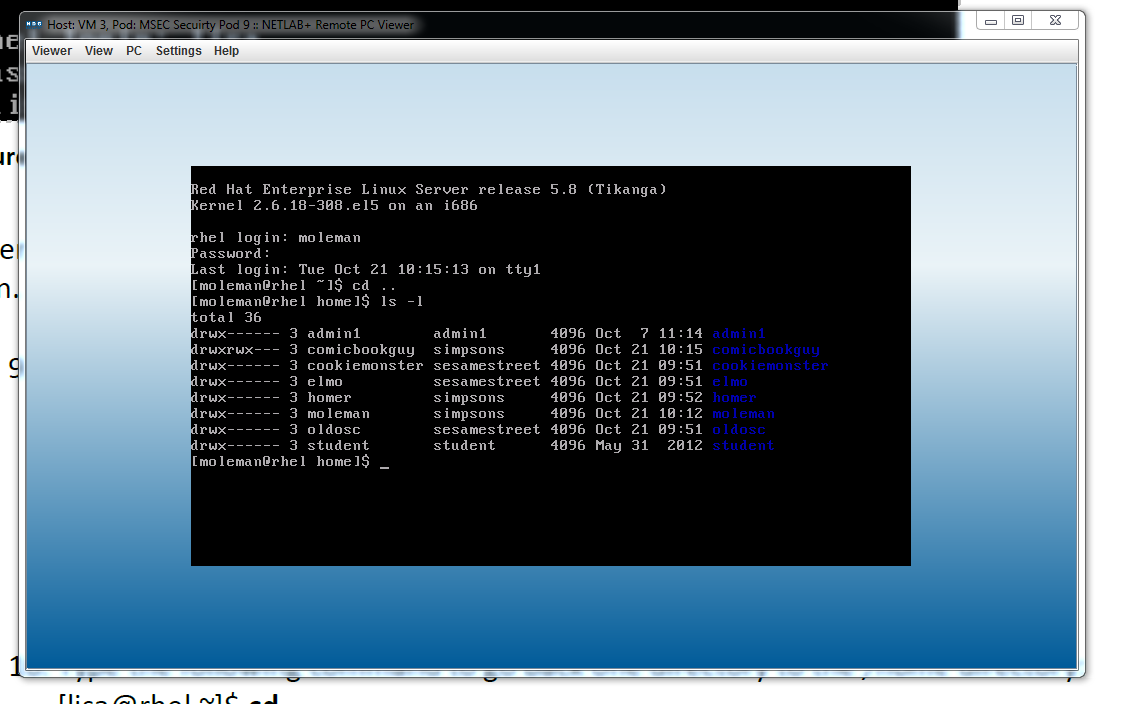 |
| This shows comic book guy naming his account read write and execute accessible |
1. What is the command to give the group read and write permissions for the comicbookguy folder, within the home directory using symbolic permissions?
chmod g+rw comicbookguy
2. What is the command to give others read permissions for the comicbookguy folder, within the home directory using symbolic permissions?
chmod o+r comicbookguy
3. What is the command to take away the read permissions for group for the comicbookguy folder, within the home directory using symbolic permissions?
chmod g-r comicbookguy
4. What is the command to take away the read and execute permissions for the others for the comicbookguy folder, within the home directory using symbolic permissions?
chmod o-rx comicbookguy
TASK 3:
In this task we used the number syntax called absolute permissions to add read write and execute options on the user account to the other users on the system and not just the ones in the group.
1. What is the command to give the user, group, and others read and write permissions for the comicbookguy folder, within the home directory using absolute permissions?
chmod 666 comicbookguy
2. What is the command to give the user, group, and others read permissions for the comicbookguy folder, within the home directory using absolute permissions?
chmod 444 comicbookguy
3. What is the command to give read and execute permissions the user, group, and others for the comicbookguy folder, within the home directory using absolute permissions?
chmod 555 comicbookguy
4. What is the command to give read, write, and execute permissions the user, group, and others for the comicbookguy folder, within the home directory using absolute permissions?
chmod 777 comicbookguy
Subscribe to:
Comments (Atom)